Lenovo XClarity Orchestrator includes a local (embedded) authentication server. You can also choose to use your own external Active Directory LDAP server.
About this task
If an external LDAP server is not configured, XClarity Orchestrator always authenticates a user using the local authentication server.
If an external LDAP server is configured, XClarity Orchestrator first attempts to authenticate a user using the local authentication server. If authentication fails, XClarity Orchestrator then attempts to authenticate using the IP address of the first LDAP server. If authentication fails, the LDAP client attempts to authenticate using the IP address of the next LDAP server.
When an external LDAP user logs in to XClarity Orchestrator for the first time, a user account with the name <username>@<domain> is automatically cloned in XClarity Orchestrator. You can add cloned external LDAP users to user groups or use LDAP groups for access control. You can also add supervisor privileges to an external LDAP user.
Procedure
To configure XClarity Orchestrator to use an external LDAP authentication server, complete the following steps.
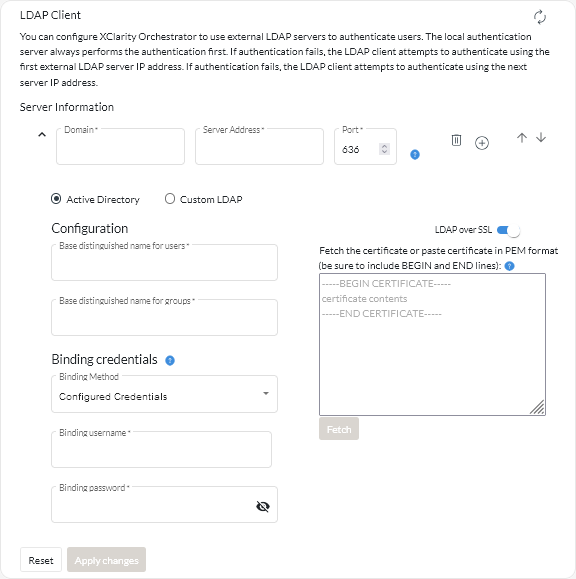
- From the XClarity Orchestrator menu bar, click , and then click LDAP Client in the left navigation to display the LDAP Client card.
- Configure each external LDAP server using the following steps.
- Click the Add icon (
 ) to add an LDAP server.
) to add an LDAP server. Specify the domain name, IP address, and port for the external LDAP server.
If the port number is not explicitly set to 3268 or 3269, the entry is assumed to identify a domain controller.
When the port number is set to 3268 or 3269, the entry is assumed to identify a global catalog. The LDAP client attempts to authenticate using the domain controller for the first configured server IP address. If this fails, the LDAP client attempts to authenticate using the domain controller for the next server IP address.
- Optionally choose to enable customizing advanced configuration settings.
When you choose to use a custom configuration, you can specify the user search filter. If you do not specify a user search filter, (&&(objectClass=user)(|(userPrincipalName={0})(sAMAccountName={0}))) is used by default.
If advanced configuration is disabled, the default Active Directory configuration is used.
- Specify the fully-qualified LDAP base distinguished name from which the LDAP client initiates the search for user authentication.
- Specify the fully-qualified LDAP base distinguished name from which LDAP client initiates the search for user groups (for example, dc=company,dc=com).
- Optionally specify credentials to bind XClarity Orchestrator to the external authentication server. You can use one of two binding methods.
- Configured Credentials. Use this binding method to use a specific client name and password to bind XClarity Orchestrator to the external authentication server. If the bind fails, the authentication process also fails.
Specify the fully-qualified LDAP distinguished name (for example, cn=somebody,dc=company,dc=com) or email address (for example, somebody@company.com) of the user account, and the password to use for LDAP authentication to bind XClarity Orchestrator to the LDAP server. If the bind fails, the authentication process also fails.
The distinguished name must be a user account within the domain that has at least read-only privileges.
If the LDAP server does not have sub-domains, you can specify the user name without the domain (for example, user1). However, if the LDAP server does have sub-domains (for example, sub-domain new.company.com in domain company.com), then you must specify the username and domain (for example, user1@company.com).
- Login Credentials. Use this binding method to use your LDAP XClarity Orchestrator user name and password to bind XClarity Orchestrator to the external authentication server.
Specify the fully-qualified LDAP distinguished name of a test user account and the password to use for LDAP authentication to validate the connection to the authentication server.
These user credentials are not saved. If successful, all future binds use the user name and password that you used to log in to XClarity Orchestrator. If the bind fails, the authentication process also fails.
You must be logged in to XClarity Orchestrator using a fully-qualified user ID (for example, administrator@domain.com).
- Optionally choose to use secure LDAP by selecting the LDAP over SSL toggle and then clicking Fetch to retrieve and import the trusted SSL certificate. When the Fetch server certificate dialog is displayed, click Accept to use the certificate.
If you choose to use LDAP over SSL, XClarity Orchestrator uses the LDAPS protocol to connect securely to the external authentication server. When this option is selected, trusted certificates are used to enable secure LDAP support.
If you choose to disable LDAP over SSL, XClarity Orchestrator uses an unsecure protocol to connect to the external authentication server. If you choose this setting, your hardware might be vulnerable to security attacks.
- Optionally reorder the LDAP servers using the Move Up icon (
 ) and Move Down icon (
) and Move Down icon ( ).
).The LDAP client attempts to authenticate using the first server IP address. If authentication fails, the LDAP client attempts to authenticate using the next server IP address.
For secure LDAP authentication, use the certificate for the root certificate authority (CA) of the LDAP server or one of the intermediate certificates of the server. You can retrieve the root or intermediate CA certificate from a command prompt by running the following command, where
{FullyQualifiedHostNameOrIpAddress} is the fully qualified name of the external LDAP server. The root CA certificate or intermediate CA certificate is typically the last certificate in the output, the last BEGIN--END section.openssl s_client -showcerts -connect {FullyQualifiedHostNameOrIpAddress}:636
- Click Apply changes.
XClarity Orchestrator attempts to test the the IP address, port, SSL certificates, and binding credentials and validates the LDAP server connection to detect common errors. If the validation passes, user authentication occurs on the external authentication server when a user logs in to XClarity Orchestrator. If the validation fails, error messages are displayed that indicate the source of the errors.
If the validation succeeds and connections to the LDAP server completes successfully, user authentication might fail if the root distinguished name is incorrect.
After you finish
Continue initial setup by going to Configuring additional security settings.